Transforming Vulnerability Management
A tidal wave of vulnerabilities, but you can’t fix them all. Rely on extensive threat intel and patented prioritization to cut costs, save time, and keep your teams efficiently focused on reducing the biggest risks to your business. This is Modern Risk-Based Vulnerability Management.
The benefits of Modern Vulnerability Management
We created Risk-Based Vulnerability Management software and now we’re defining the modern model
Confidence
In our experience and full-stack, real-time view
Intelligence
With evidence-based guidance and predictive data science
Alignment
Between Security and IT on priorities, actions, and measures
Why Kenna?
Focus on risk with Modern Vulnerability Management
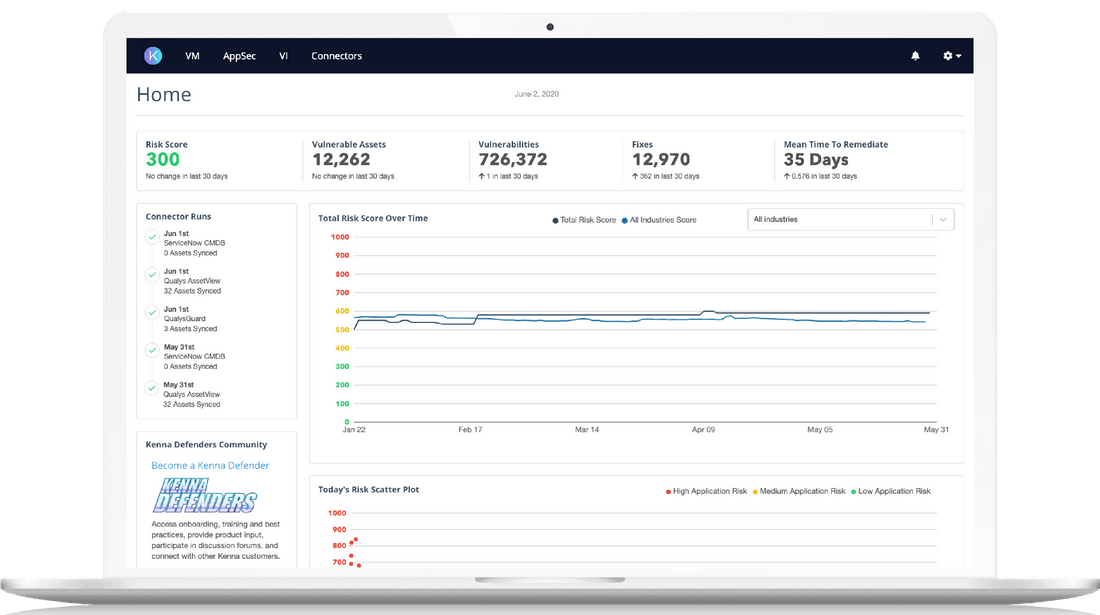
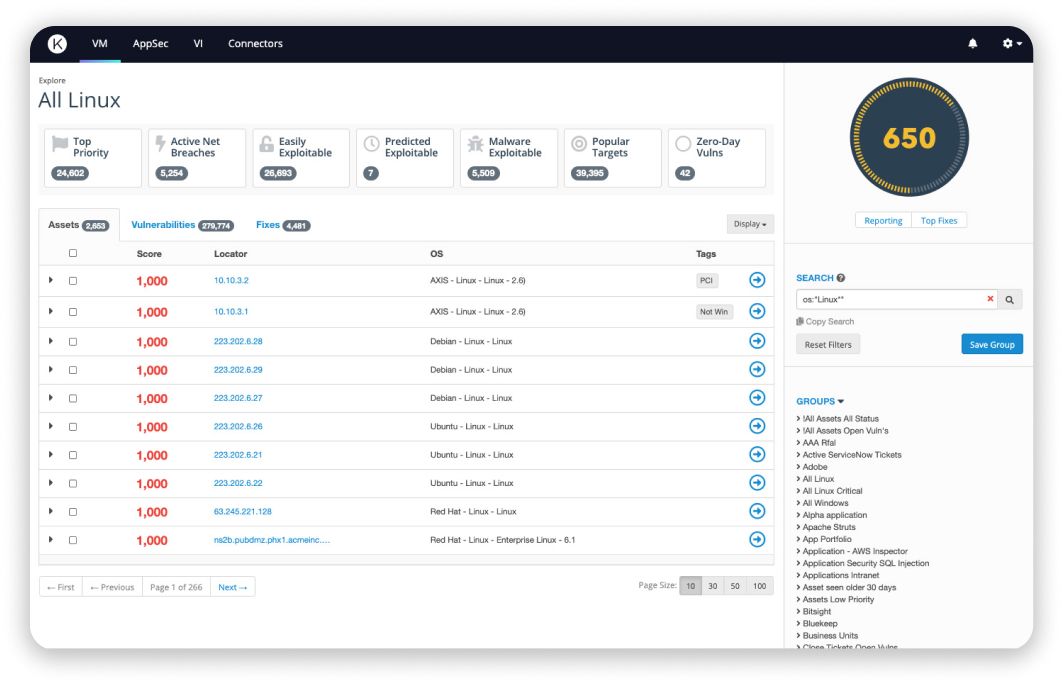
Kenna.VM
Remediate what matters most
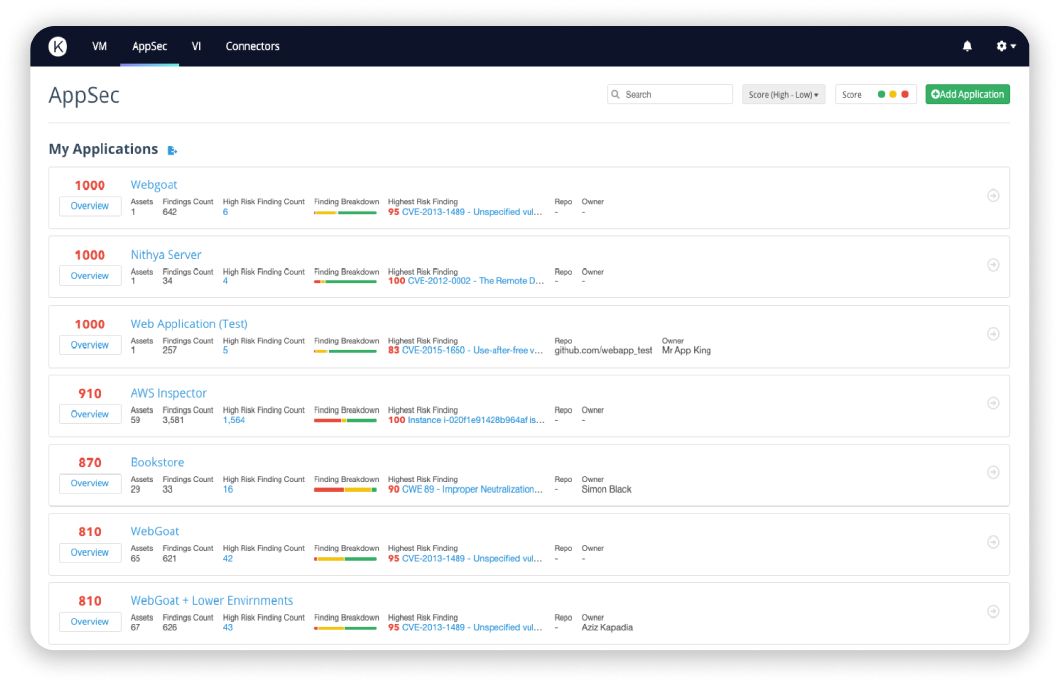
Kenna.AppSec
Up-level application security
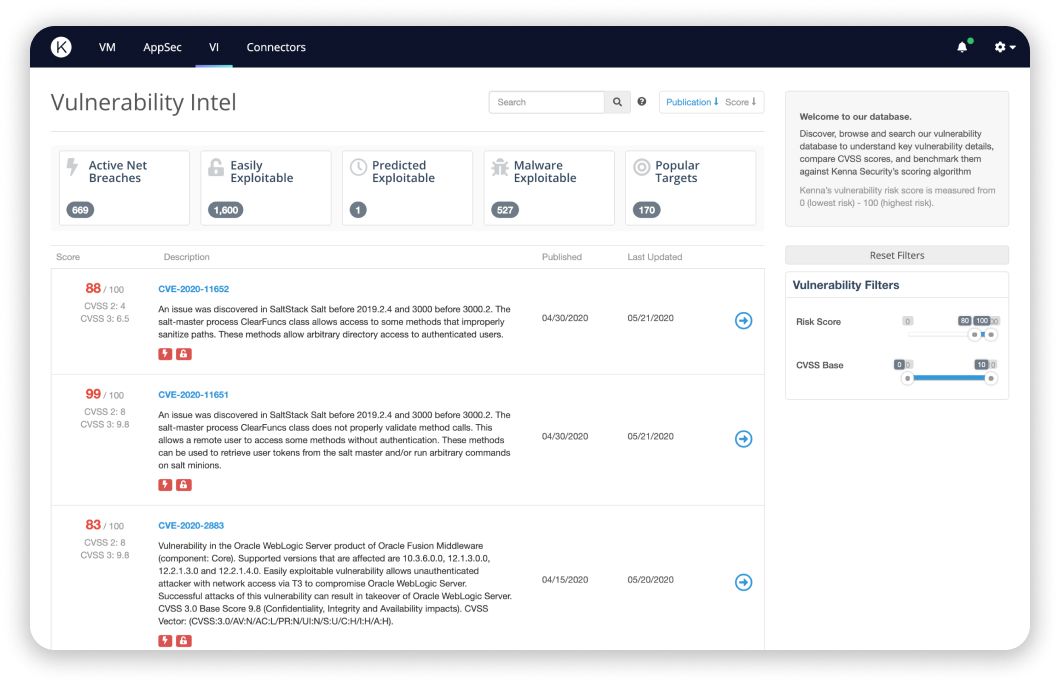
Kenna.VI
Access vital threat intel
Show your security and IT teams which infrastructure vulnerabilities they should remediate, when.
Empower your AppSec, development, and DevOps teams to accurately assess, track, and prioritize application vulnerabilities by risk.
Access to a comprehensive database of threat and exploit intelligence-enriched vulnerabilities to answer critical research questions.