Research Reports
Cutting-edge research on vulnerability management
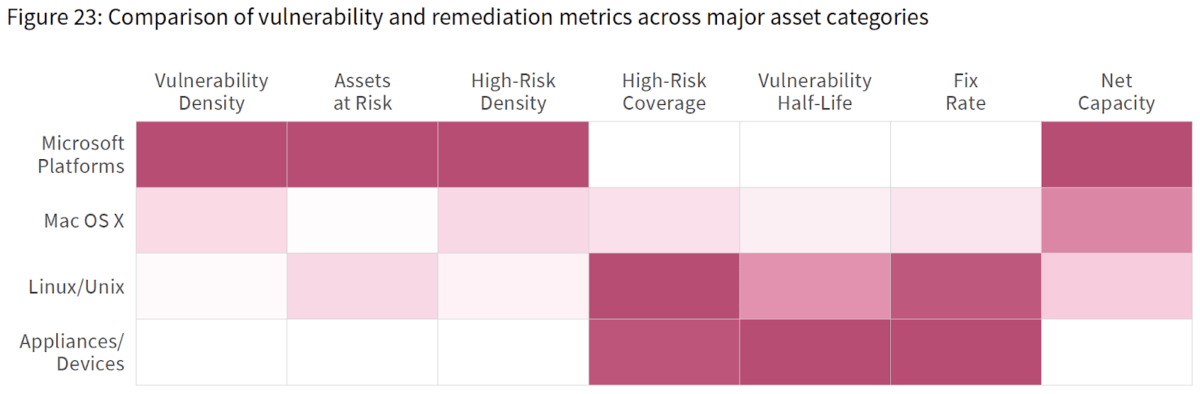
P2P Volume 5: In Search of Assets at Risk
The fifth volume of the Prioritization to Prediction series produced in conjunction with the Cyentia Institute explores the vulnerability risk landscape by looking at how enterprises often view vulnerabilities: through the lens of common asset platforms.
Download NowResearch
Posture Perfect: 5 Tips for Straightening up Your Vulnerability Management Program
Recent survey findings reveal promising strategies for teams looking to straighten up their security posture.
READ MORE
Research
Supply Chain Security 101: Understanding Your Supply Chain and Your Risks
"Supply chain security” may be the latest buzzword but few know what it really means or how to approach it. Get expert insight into understanding your...
READ MORE
Research
How Improving Security Resilience Reduces Business Risk
Enterprise leaders are recognizing that security resilience reinforces business resilience and lowers overall risk, but the road to a resilient future...
READ MORE
Research
8 Biggest VM Implementation Pitfalls (And How to Avoid Them)
We’ve assembled an all-star lineup to unpack the biggest missteps facing RBVM implementations—and the best ways to maximize ROI and lower risk.
READ MORE
eBooks
Buy vs. Build? 5 Considerations for Vulnerability Management
Download an eBook to help determine when to buy, when to build, or when to do both when it comes to employing a vulnerability management program that...
DOWNLOAD NOW
eBooks
How to Build a Modern VM Program in 6 Steps
A buyer's guide that walks prospects through the 6 steps needed to implement a risk-based vulnerability management program.
DOWNLOAD NOW
How to Implement Risk-Based Vulnerability Management Now: A Practical Guide
Download the guide and discover why traditional ways of vulnerability management no longer work and how focusing on risk is the key to remediating the vulnerabilities that matter most.
eBooks
7 Questions to Ask Every Vulnerability Management Vendor
Download an eBook outlining the 7 pivotal questions security decision-makers need to ask when comparing vendor effectiveness.
DOWNLOAD NOW
Research
How Machine Learning Models Can Uncover the True Causes Behind Breaches
Machine-learning techniques can help SOC analysts better analyze and decipher the millions of alerts they see, and to find the alerts that matter most.
READ MORE
Research
How to Squeeze the Most Risk Reduction from Your Vulnerability Management
The latest cybersecurity research is in: Better vulnerability management starts with a better understanding of exploitability.
READ MORE
Research
Remediate faster, more efficiently with data-driven risk prioritization
The latest addition to the Cisco security portfolio, Kenna Security, enables organizations to manage infrastructure security risk.
READ MORE
Research
(Un)usual Suspects: Top Vulns That Flew Under the Radar in 2021
For everyone in the cybersecurity space, 2021 has been a doozy. The last 12 months have had a kind of “take no prisoners” energy.
READ MORE
Research
How To Predict the Next Big Exploit
In this webinar we unpack how to predict the next big exploit. We'll go from theory to practice, from past to present with a bit of future.
READ MORE