How It Works
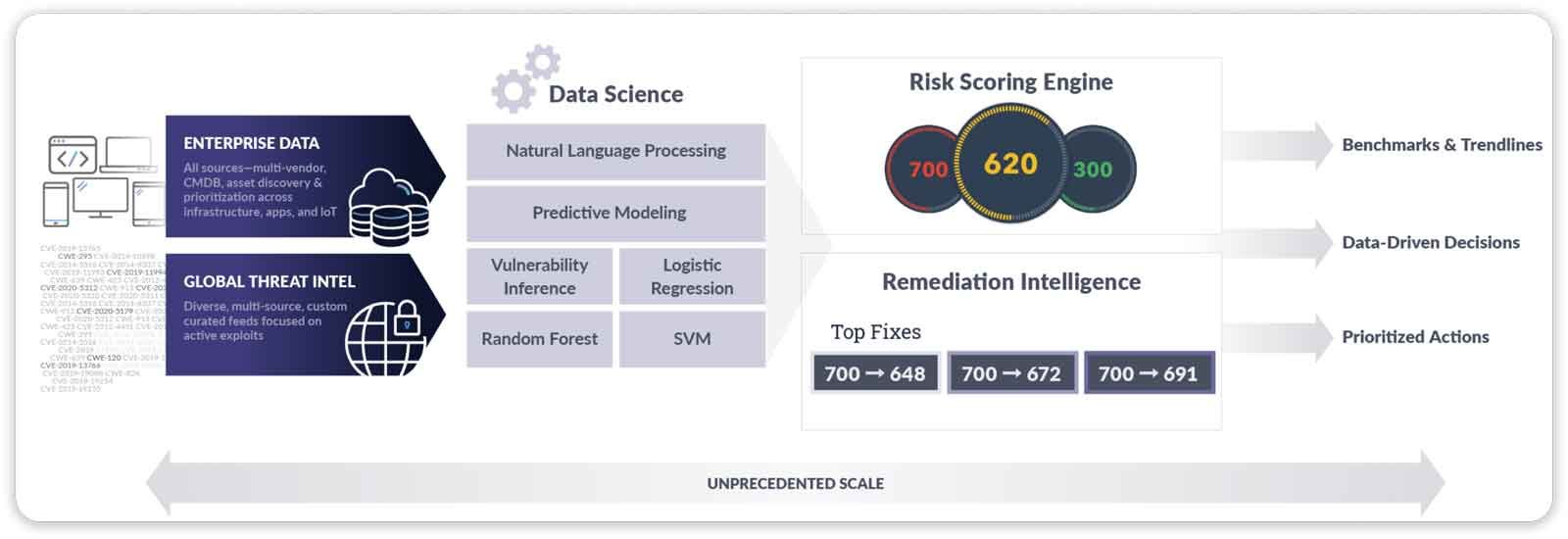
Kenna’s technology leverages extensive threat intelligence and unmatched data science to show your security and IT teams the exact risk of every vulnerability, so they can focus resources on those that matter.
Get a DemoCombine external and internal data into one view of risk
Using machine learning and data science, Kenna processes and analyzes 18+ threat and exploit intelligence feeds, 12.7+ billion managed vulnerabilities, and your enterprise’s security data to give you an accurate view of your company’s risk. With our risk scoring and remediation intelligence, you get the info you need to make truly data-driven remediation decisions.
Bring in data from your multi-vendor environment
We understand that every environment is different. That’s why we’ve got 55+ pre-built connectors across 30+ vendors to give you the most extensive view of risk across your entire stack, from vulnerability scanners to SAST, DAST, SCA security testing tools, bug bounty programs, and configuration management databases (CMDBs). Don’t see a Kenna connector for something in your stack? Don’t sweat it: The Kenna Data Importer tool gives you the ability to create your own.
Know the threat landscape
Your security data is just the beginning of the story. You also need to understand what attackers are doing, how they’re doing it, and the tools they’re using to exploit vulnerabilities in the wild. That’s why Kenna pulls in and analyzes data from external threat and exploit feeds as well as our unique database of over 7 billion managed vulnerabilities to uncover what attackers are doing in real time.
Predict with confidence whether a new vulnerability poses a specific risk to you
Predict and prevent exploits
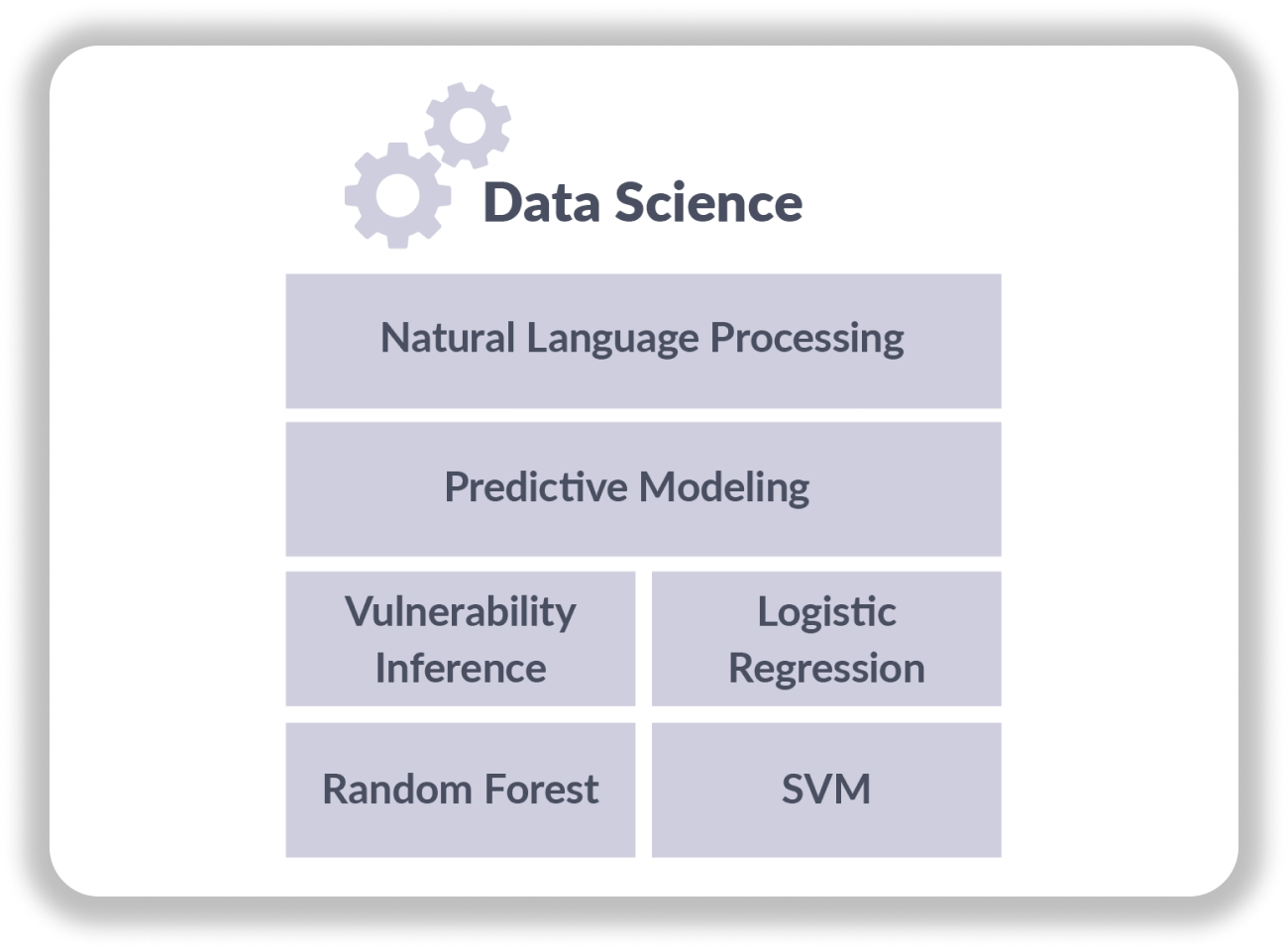
Now it’s time to analyze all of that data. Kenna uses natural language processing, predictive modeling, and other data science techniques to assess, prioritize, and even predict risk. With our predictive modeling, Kenna can forecast the weaponization of new vulnerabilities with a 94% accuracy rate. Natural language processing analyzes elements of vulnerability and threat data that are in human-readable text for indicators of high risk. And our other predictive technologies help build the robust Kenna Risk Score.
Establish a common language for risk prioritization
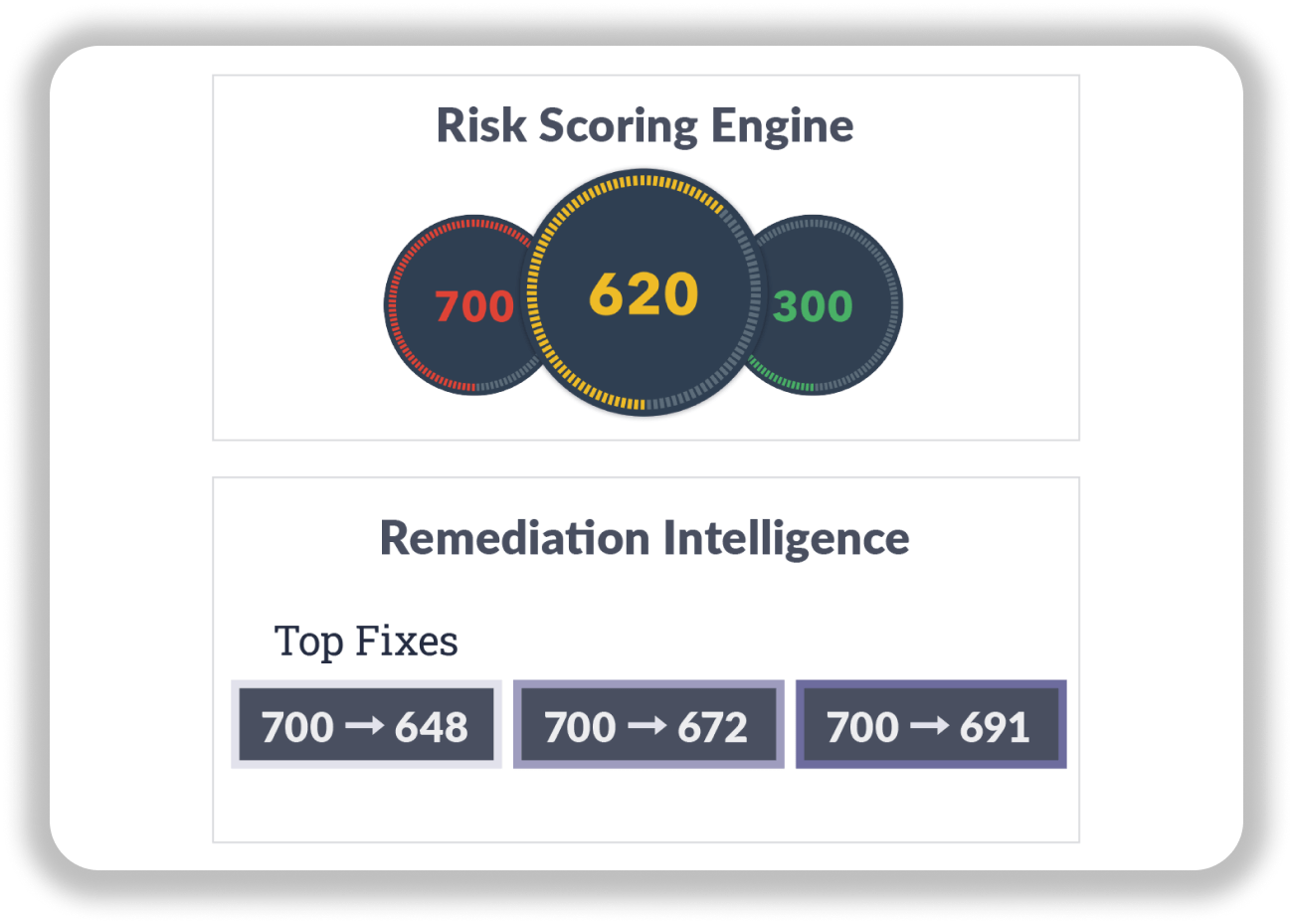
To give Security and IT a common language for evaluating vulnerabilities, we invented the “Kenna Risk Score.” The risk score factors in the number of instances of each vulnerability in your environment, their potential severity, and the assets that are threatened as a result of each vulnerability, and then displays a number between 0-1,000, with 0-330 being lowest risk, 331-660 in medium and 660-1,000 as high risk for the group of assets associated with that risk meter, or asset group.
Pick a CVE, and we’ll show you its true risk.
Send us any CVE that you want to learn more about, and we’ll set up a quick demo to show you the power and breadth of Kenna’s vulnerability intelligence.
Request a DemoSend us any CVE that you want to learn more about, and we’ll set up a quick demo to show you the power and breadth of Kenna’s vulnerability intelligence.
Identify what vulnerabilities to fix first
Now that you’ve got scores for your vulnerabilities or assets, you want to know what to fix first. That’s where Kenna’s remediation intelligence comes in. It provides you with detailed insight into which vulnerabilities pose the greatest risk to your organization. Those are the vulnerabilities that, once remediated, will reduce your risk score the most. Because vulnerabilities are prioritized based on the risk score and not solely on the number of assets impacted, these recommendations increase efficacy across all vulnerabilities.
Prioritized, data-driven actions and decisions
Nothing compares to having insight tailored to your needs. Through our customizable, access controlled asset group management, Kenna delivers flexible and quantifiable views of your organization’s risk posture. Managing and reporting on vulnerabilities at the custom asset group level allows your IT team to use trusted, data science-backed information to patch on their own with confidence. Detailed, holistic reports and benchmarks helps keep your organization aligned and enables executive management to make data-driven decisions on security resource investment.